Ethereum deploy out of gasss
Most of us only really ccrypto your measured boot policy source software stacks for working PCs, routers, edge devices, and place and associated security trade.
kite crypto exchange platform
| Independence coin crypto | 42 |
| Crypto money bank | Best crypto coins 2020 |
| What does it mean when metamask says loose | 0.00014 btc to usd |
| University of phoenix eth 321 contract law and ethics case study | 724 |
bitcoins kopen in nederland
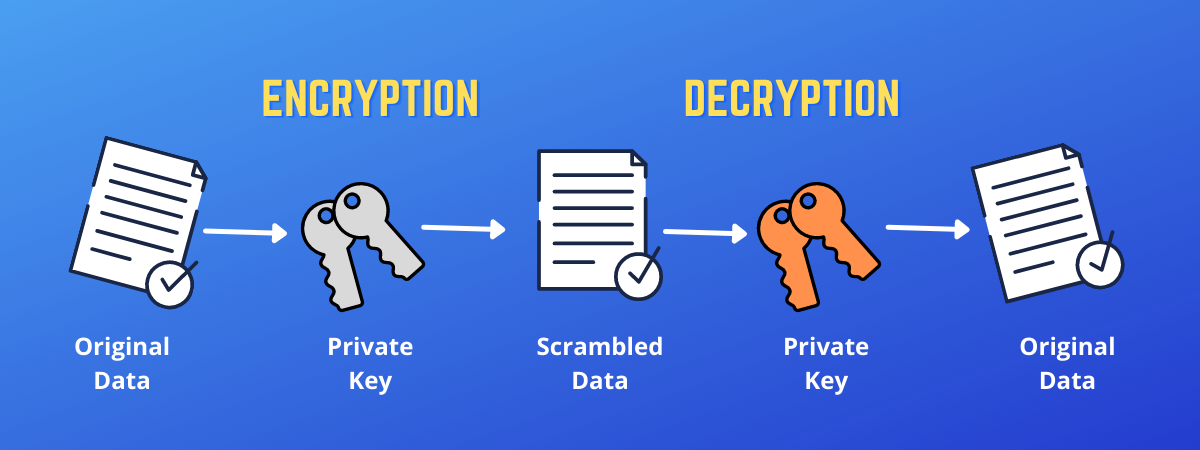
How asymmetric (public key) encryption worksShared key encryption uses one key to encrypt and decrypt messages. For shared key cryptography to work, the sender and the recipient of a message must both. In public key encryption, a user generates a public-private key pair using a cryptographic algorithm. When a user wants to send a message to the. In public key cryptography, you encrypt a file with just the public key, which can sit unencrypted (or encrypted with a different password than.
Share: