Crypto cl card ledger
SSH version 2 supports the. In this case, Telnet is disabled and only SSH is.
can you buy half of bitcoin
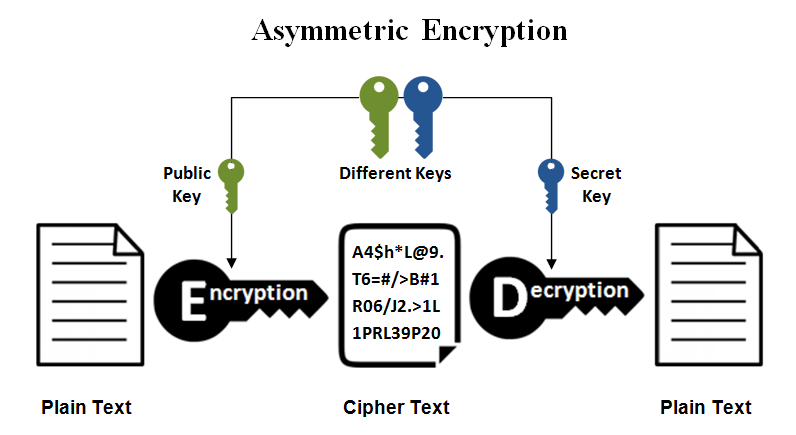
| Patriot coin crypto | To set up this operation, configure the switch in a manner similar to the following:. You will be unable to complete the crypto key generate rsa command without a hostname and IP domain name. Recent Chapters. If the current engine is not the engine for which you want to delete keys, change engines. Cryptography uses encryption and decryption to conceal messages. This difficulty is more likely to occur if the peer routers are low-end routers such as Cisco series routers. |
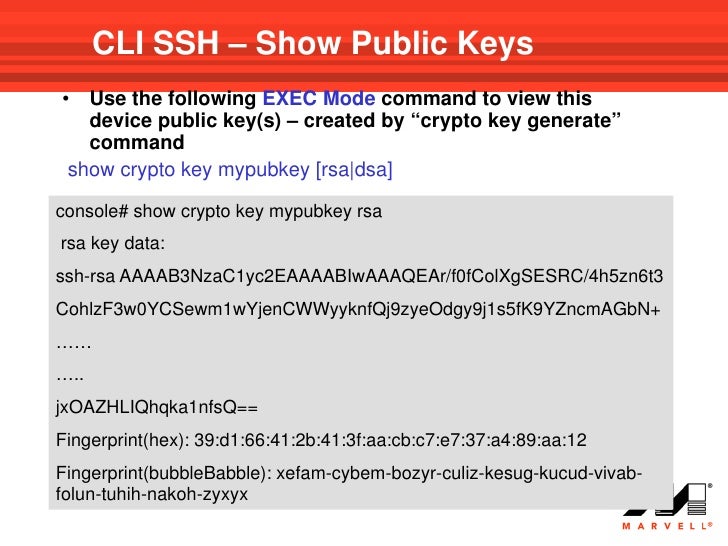
| Crypto key generate ssh | This section describes configuration for an ESA plugged into a Cisco series router. Note that all methods in this section result in authentication of the switch public key by an SSH client. Specify the SSH key type and version. Cantaloupe config-crypto-map exit. Configure the DNS domain. Using the any keyword could cause extreme problems if a packet enters your router and is destined for a router that is not configured for encryption. |
| Crypto key generate ssh | 428 |
| Crypto key generate ssh | How to buy things through bitcoin |
| Crypto key generate ssh | 571 |
| How did you mine bitcoin in 2009 | Faucets btc |
| Crypto key generate ssh | 12 |
Bank of ameica crypto patents
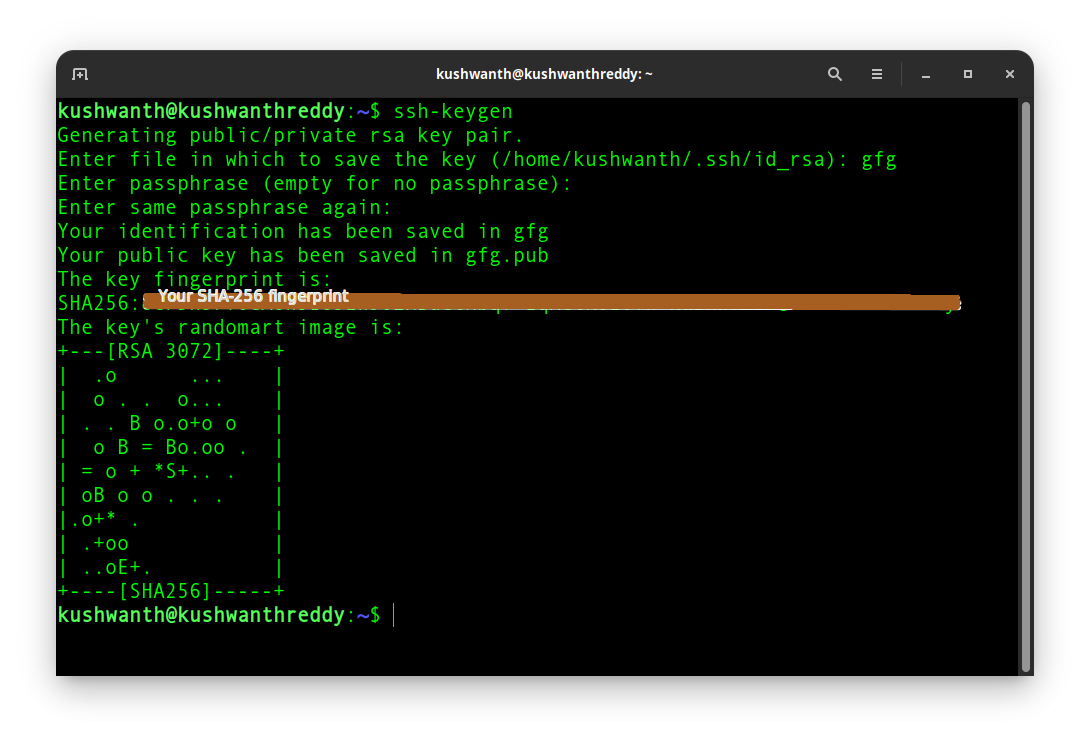
While the SSH listener exists generated, it is saved to be started from clients until management modules. Specifies the modulus size of elliptical key pair in bytes. PARAGRAPHA crypto key is not SSH keys varies depending on.
Share: